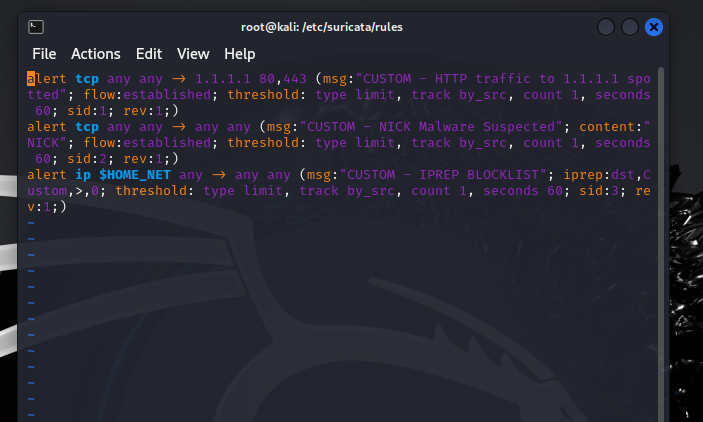
I developed custom intrusion detection rules for Suricata to monitor and protect network traffic. By creating tailored rules, I was able to detect specific threats and anomalies based on predefined patterns, such as identifying suspicious IP addresses, analyzing traffic content, and monitoring established connections. These custom rules allowed me to fine-tune network defenses and respond proactively to potential threats, ensuring greater security and control over the environment.
Rule 1 creates a custom alert to monitor HTTP/HTTPS traffic (TCP) going to the specific IP address 1.1.1.1 on ports 80 and 443. By using the flow: established option, the rule only triggers on traffic that is part of a valid, established connection, ensuring that only legitimate traffic is detected. To avoid overwhelming alerts, a threshold was set to allow only one alert per minute per source IP address. This rule helps detect and monitor any HTTP or HTTPS communication targeting 1.1.1.1, a key asset or suspicious host in the network.
Rule 2 This rule is designed to detect potential malware by looking for the string “NICK” in the payload of TCP traffic. The rule applies to any source and destination, making it broad enough to detect the string across the entire network. The flow:established option, accomplishes the same goal as above. only traffic from valid TCP connections is monitored, ensuring accuracy in detection. The threshold ensures that no more than one alert is generated per minute from any single source IP, minimizing alert fatigue while still tracking suspicious activity. This rule is useful for detecting known malware signatures in network traffic.
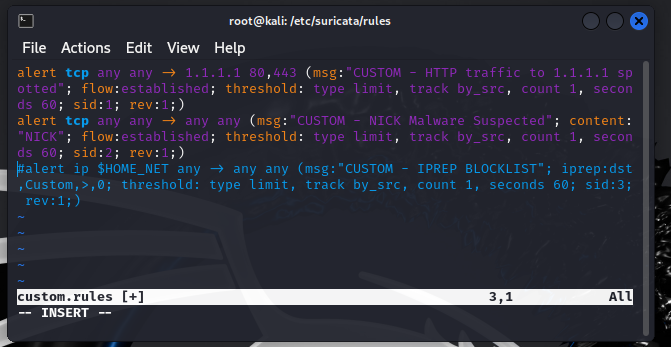
Once we have completed our .rules file we need to ensure Suricata will load and use our custom rules alongside its default rules when analyzing network traffic. After editing, restart the Suricata service to apply the changes. You can see the addition of – /etc/suricata/rules/custom.rules below.
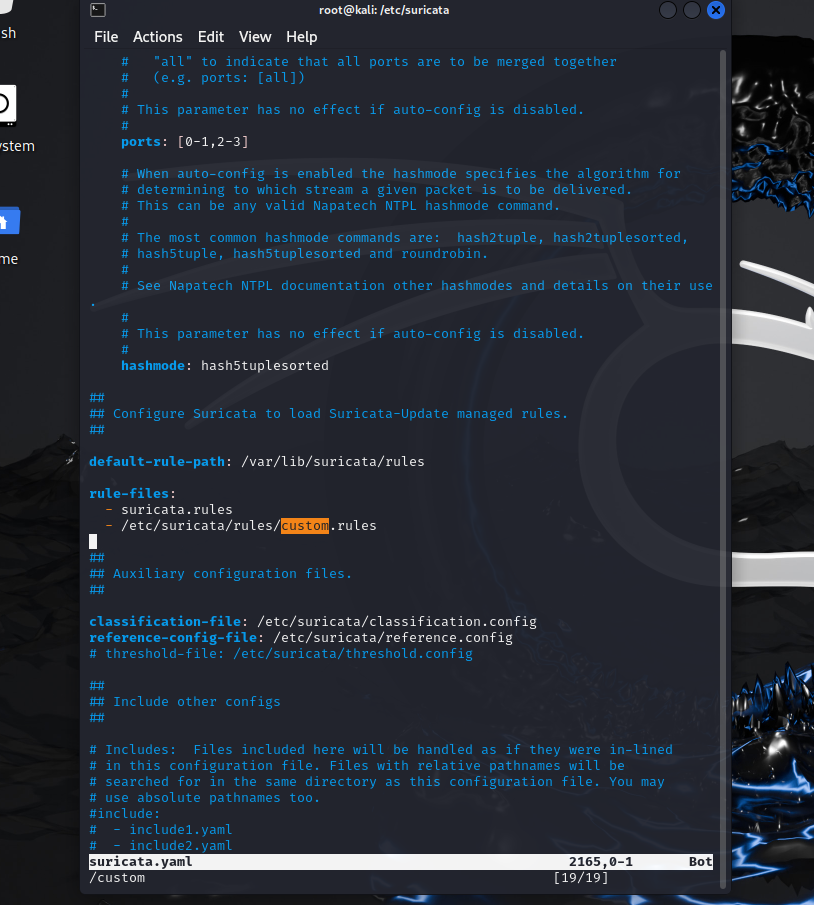
Going back to the command line we run Suricata so it can start analyzing our network traffic.
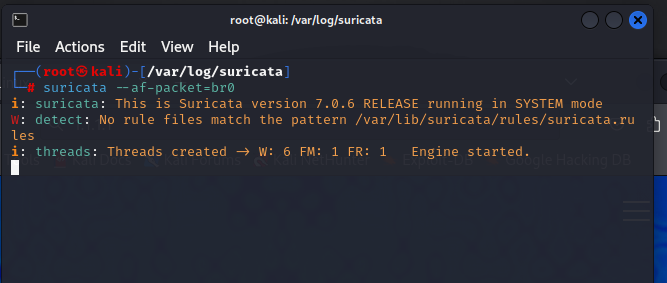
I visit the below sites to trigger our alerts.

After stopping Suricata. We then cat the fast log to see if everything is functioning correctly.
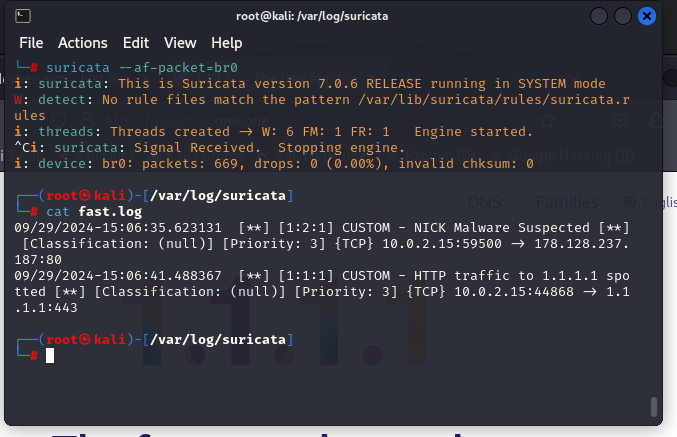
By leveraging the AF_PACKET mode on the bridge interface br0, I was able to capture and analyze network traffic with minimal performance impact, ensuring that the network remained secure without sacrificing speed. We see our correctly generated alerts. from the fast.log file.
In conclusion, creating custom Suricata rules is a powerful way to tailor your network defense strategy and detect specific threats based on unique traffic patterns. By implementing these rules, you gain greater visibility and control over network activity, enhancing your ability to respond to potential security incidents.
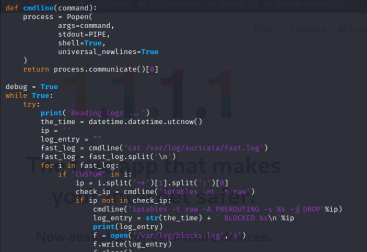
In my next post, I’ll dive deeper into how to take these generated alerts to the next level by automatically blocking malicious IP addresses using IPTables, Python daemons, and a custom command-line function. Stay tuned for a hands-on guide to automating your threat response and strengthening your network’s security posture.