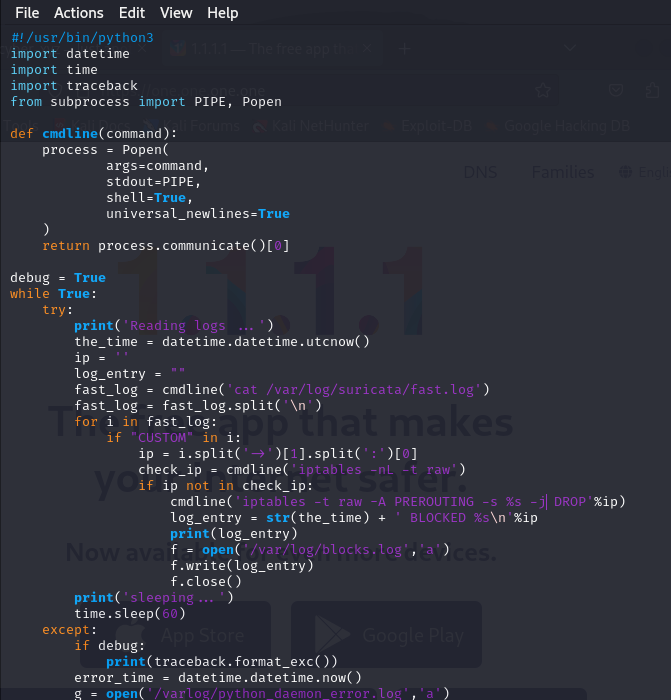
In this project, I developed a program designed to automatically detect and block malicious external IP addresses based on alerts generated by Suricata’s fast logs. The program reads the log files, identifies any alerts that meet predefined criteria for blocking, and then takes action by adding the offending IP addresses to the system’s firewall using iptables.
This solution leverages the power of Linux, integrating Python scripts, Python daemons, and command-line tools to automate the process of identifying and blocking potentially harmful traffic. By creating a streamlined, efficient process to manage network security alerts, this project demonstrates practical applications of Python in cybersecurity for real-time threat mitigation.
The following steps are a continuation of my building custom Suricata rules post. If you have not seen it please find it here. We begin with our python daemon program.
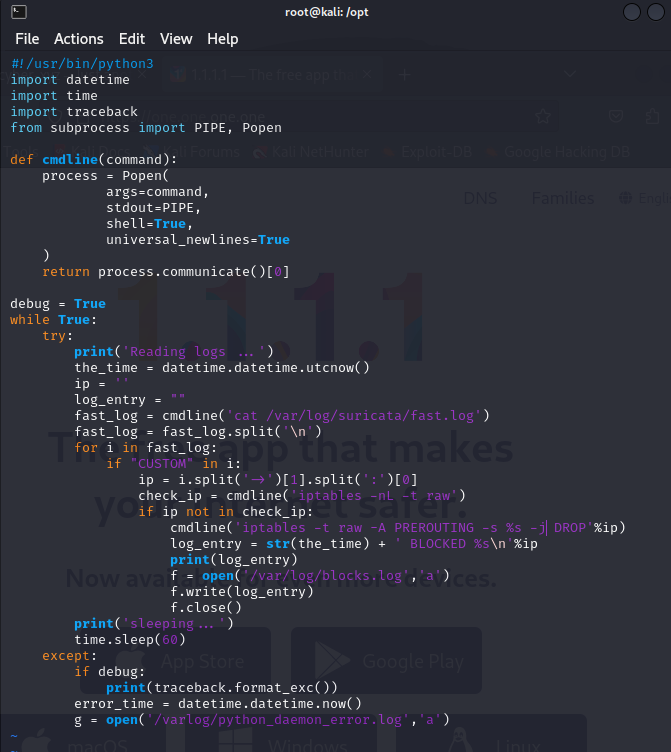
This script continuously reads the Suricata fast log, checks for alerts that contain the keyword “CUSTOM,” extracts the IP address, checks if it’s already blocked in iptables, and blocks it if necessary. It logs the blocked IPs to /var/log/blocks.log and any errors to /var/log/python_error.log.
We will be using supervisor to manage our python daemon, so we have to place in the configuration file for supervisor.
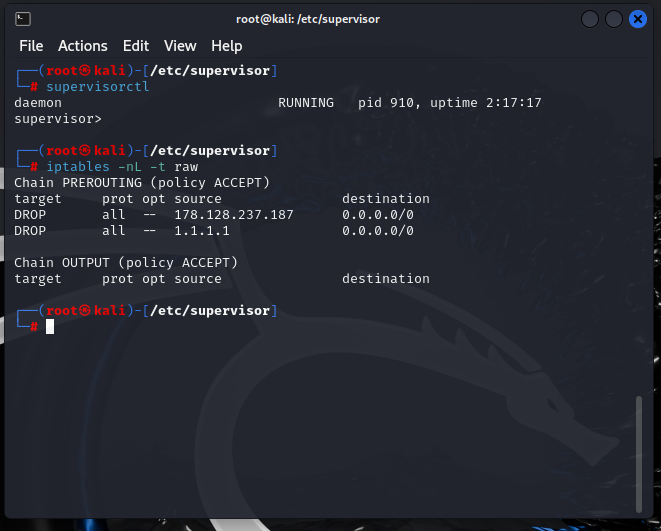
By using the supervisorctl command, we can monitor all available daemons and confirm that our custom daemon is running. Once verified, we check the firewall with iptables and observe that, according to our custom rules, the IP addresses 178.128.237.187 and 1.1.1.1 have been successfully blocked.
In order to use this effectively and block possibly hundreds of IP addresses we need to utilize IP Reputation, which is turned off by default in Suricata. We navigate over to our YAML file to activate it. Under # IP Reputation we see a few lines that will be commented out by default. We see here that i have already removed the # and added in my directory.
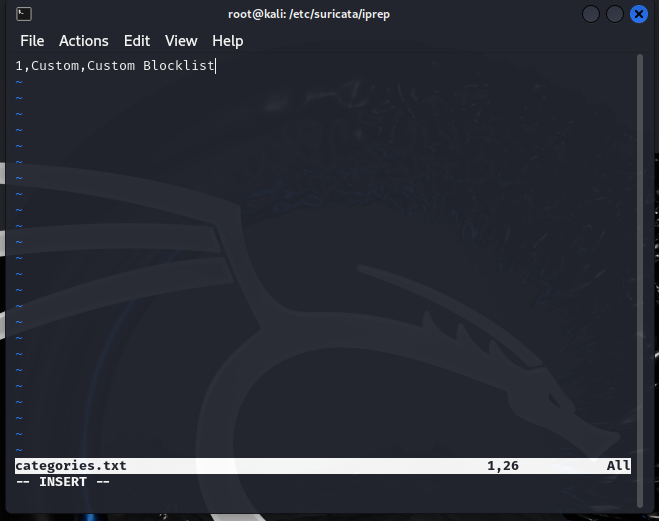
In my categories.txt file for IP reputation in Suricata, I created a custom blocklist category with the ID 1. The entry 1,Custom,Custom Blocklist defines this category. The identifier “Custom” allows me to link specific IPs to this blocklist, while the description “Custom Blocklist” helps me manage and track blocked IPs easily. By using this setup, I can efficiently monitor and block any incoming or outgoing traffic from known or suspicious IPs through my custom reputation rules.
In my reputation.list file, I’ve added the CIDR block 1.0.0.0/24, which includes all IPs from 1.0.0.0 to 1.0.0.255. This range is assigned to the custom blocklist category with the ID 1, which I set up in the categories.txt file. The second 1 indicates the priority of the blocklist entry. This setup ensures that any traffic from IPs within this range is flagged and blocked by Suricata, providing an additional layer of security for my network.
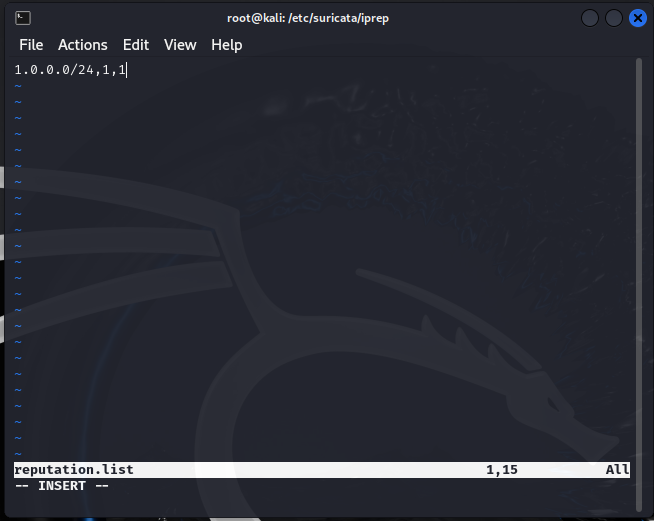
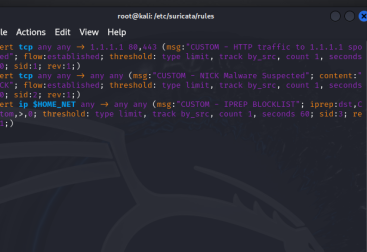
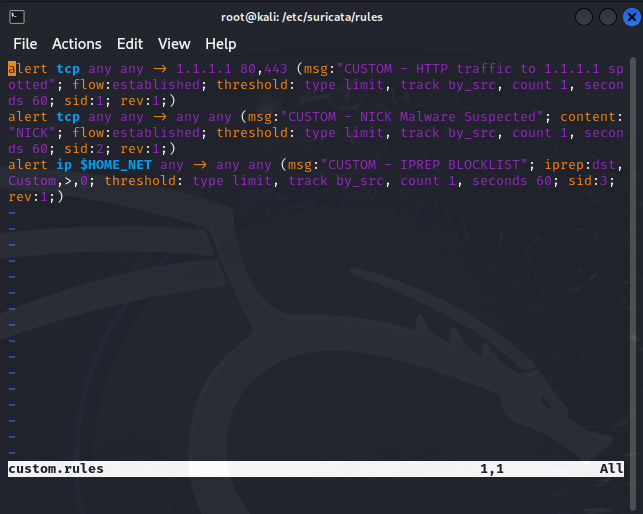
Taking a look at our rule that it alerts when any traffic from the home network ($HOME_NET) is directed to an IP that appears on a custom IP reputation blocklist. It checks the destination IP (iprep:dst) against this list and triggers an alert if found. The rule limits alerts to one per minute per source, preventing repetitive notifications.
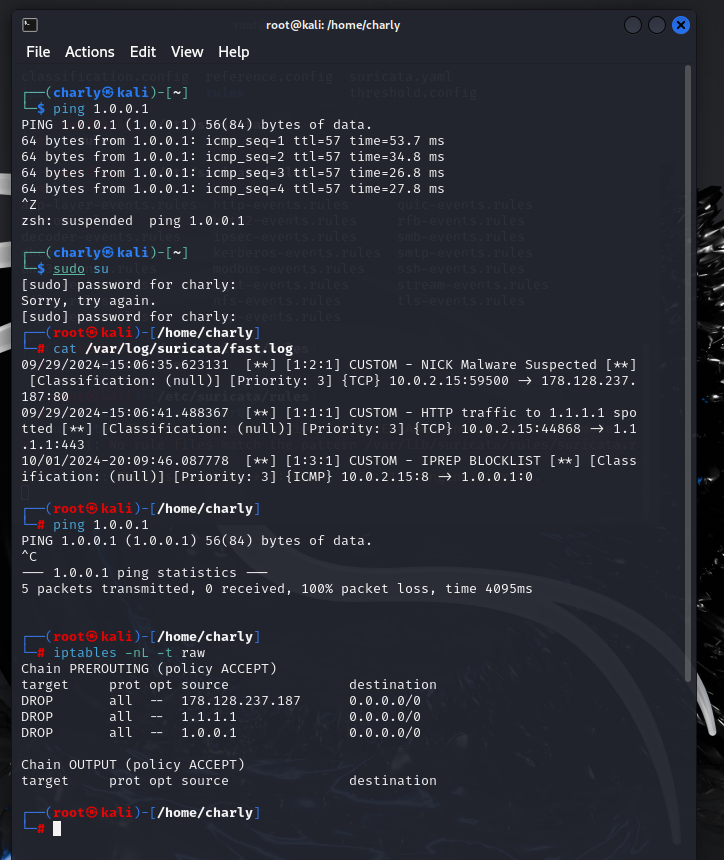
We can see this in action with the below steps. I am able to ping 1.0.0.1 successfully at first. We cat the fast log after to see we received an alert. Retrying to ping 1.0.0.1 again results in complete packet loss. Checking our iptables we now see that 1.0.0.1 is blocked.
In conclusion, building this custom firewall using Suricata showcases my ability to work with intrusion detection systems, Linux, and Python to automate network security tasks. It highlights my skills in writing custom rules, managing IP reputation, and utilizing iptables for real-time threat mitigation. This project demonstrates my competency in creating practical security solutions, which is essential in the cybersecurity job market. By blending scripting, automation, and firewall management, I am well-prepared to tackle challenges in securing networks and protecting against malicious activities.