Capturing a password using TCP dump & Wireshark
Coming soon….
Coming soon….
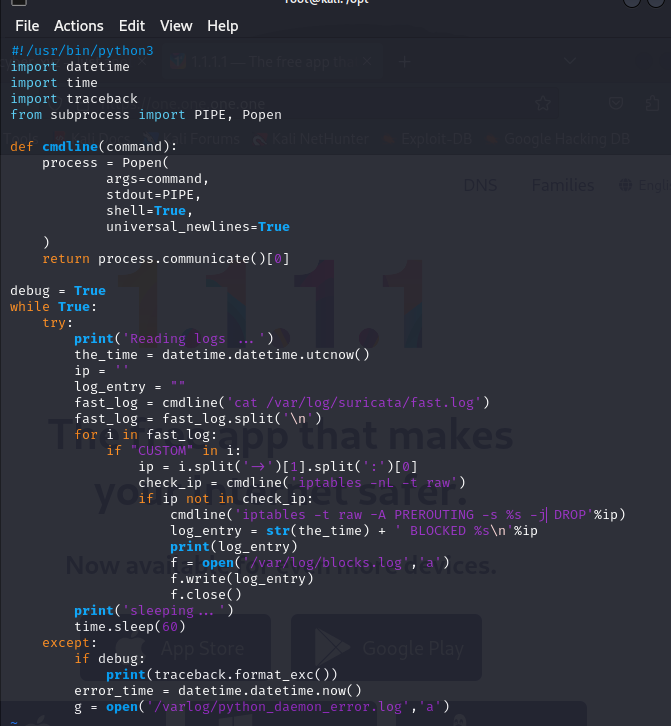
In this project, I developed a program designed to automatically detect and block malicious external IP addresses based on alerts generated by Suricata’s fast logs. The program reads the log files, identifies any alerts that meet predefined criteria for blocking, and then takes action by adding the offending IP addresses to the system’s firewall using …
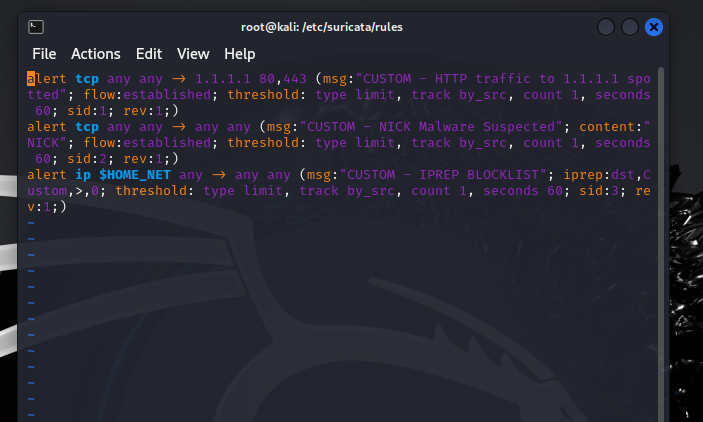
I developed custom intrusion detection rules for Suricata to monitor and protect network traffic. By creating tailored rules, I was able to detect specific threats and anomalies based on predefined patterns, such as identifying suspicious IP addresses, analyzing traffic content, and monitoring established connections. These custom rules allowed me to fine-tune network defenses and respond …
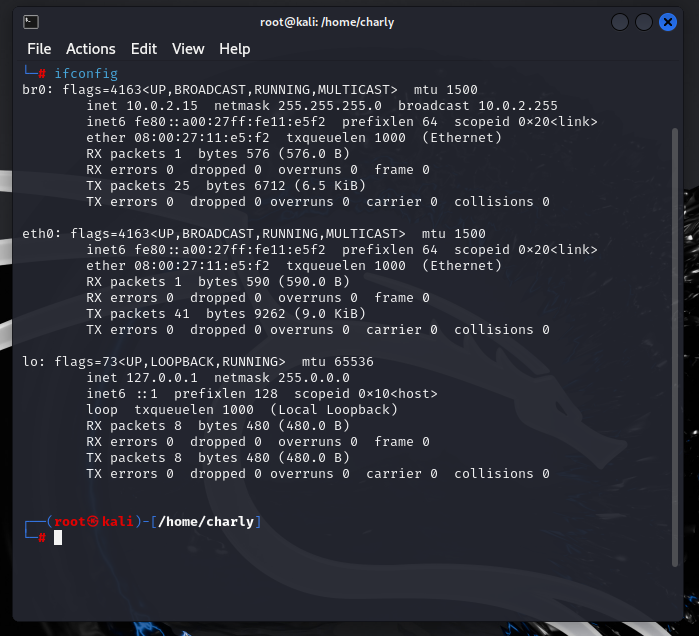
Creating a transparent bridge in Linux is an essential skill for anyone looking to monitor or control network traffic without interfering with the flow of data. A transparent bridge operates at Layer 2 of the OSI model, forwarding packets between network interfaces without modifying them, making it invisible to the devices on the network. In …